Phase 3 – Containment & Communication
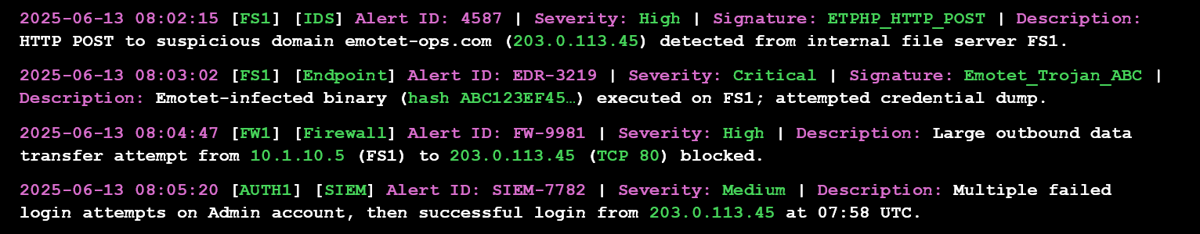
Following detection of the Emotet malware incident, ACME’s incident response team immediately moved to contain the breach and communicate with affected parties. In line with best-practice guidance, the team isolated infected hosts, preserved evidence, and began coordinating notifications. The timeline below summarizes key containment actions over the first 72 hours:
-
Day 1, 09:00: IT detects unusual network traffic and a suspicious email with a malicious attachment. Incident Response (IR) team is activated.
-
Day 1, 09:10: Preliminary analysis identifies Emotet trojan (spread via malspam) as the culprit. The infected workstation is disconnected from the network.
-
Day 1, 09:20: All affected systems are quarantined and offline to halt the spread (“isolate affected systems”). Antivirus signatures and firewall rules are updated to block the Emotet payloads and command-and-control servers.
-
Day 1, 10:00: Emergency meeting with senior management and compliance. Legal/regulatory teams are alerted and prepared to notify authorities.
-
Day 1, 10:30: National CSIRT is notified with an early warning (per NIS2 Article 23, within 24 hours) that a malicious Emotet incident has been detected and is under investigation. It is reported as malicious and with no expected cross‑border impact.
-
Day 1, 13:00: Full network scan and endpoint audits begin. Persistence mechanisms (scheduled tasks, registry entries, services) are identified in line with Emotet behavior. IR team removes Emotet services and cleans infected hosts.
-
Day 1, 15:00: All potentially compromised user and administrator credentials are reset and multi-factor authentication is enforced to block unauthorized access. Network segmentation is enforced for critical banking systems.
-
Day 1, 16:00: Internal communications drafted. The executive team convenes to approve external messaging to customers and staff.
-
Day 2, 09:00: Forensic analysis continues; no evidence of data exfiltration is yet confirmed. IR team completes eradication of Emotet from identified hosts and performs additional scans on backups.
-
Day 2, 11:00: Regulatory/legal team prepares the 72-hour incident notification. Draft customer advisory email and staff advisories are reviewed.
-
Day 2, 14:00: Press office prepares statements. We verify contingency plans to ensure continuity of banking services.
-
Day 3, 09:00: Containment verified: all infected endpoints cleaned or reimaged, critical systems monitored for anomalies. The formal 72-hour incident notification report is finalized and submitted to the national CSIRT, as required by NIS2 Article 23.
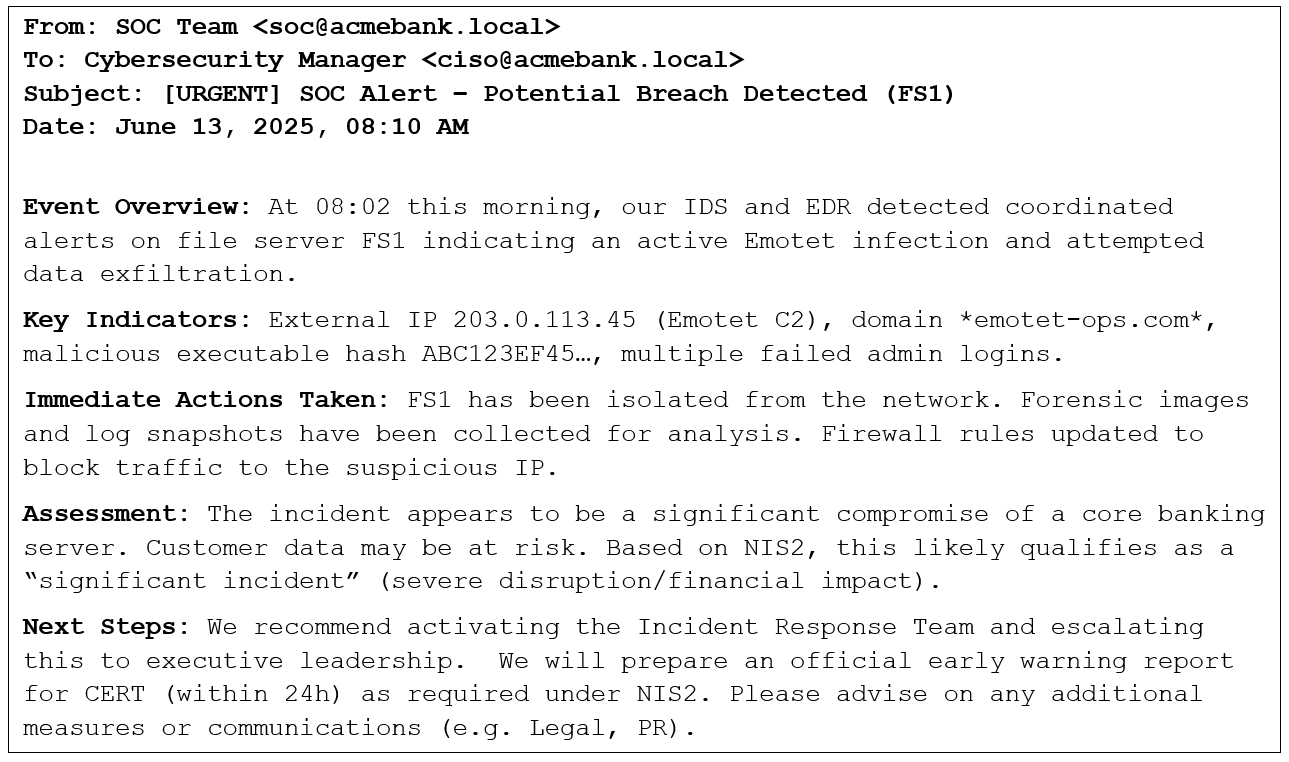
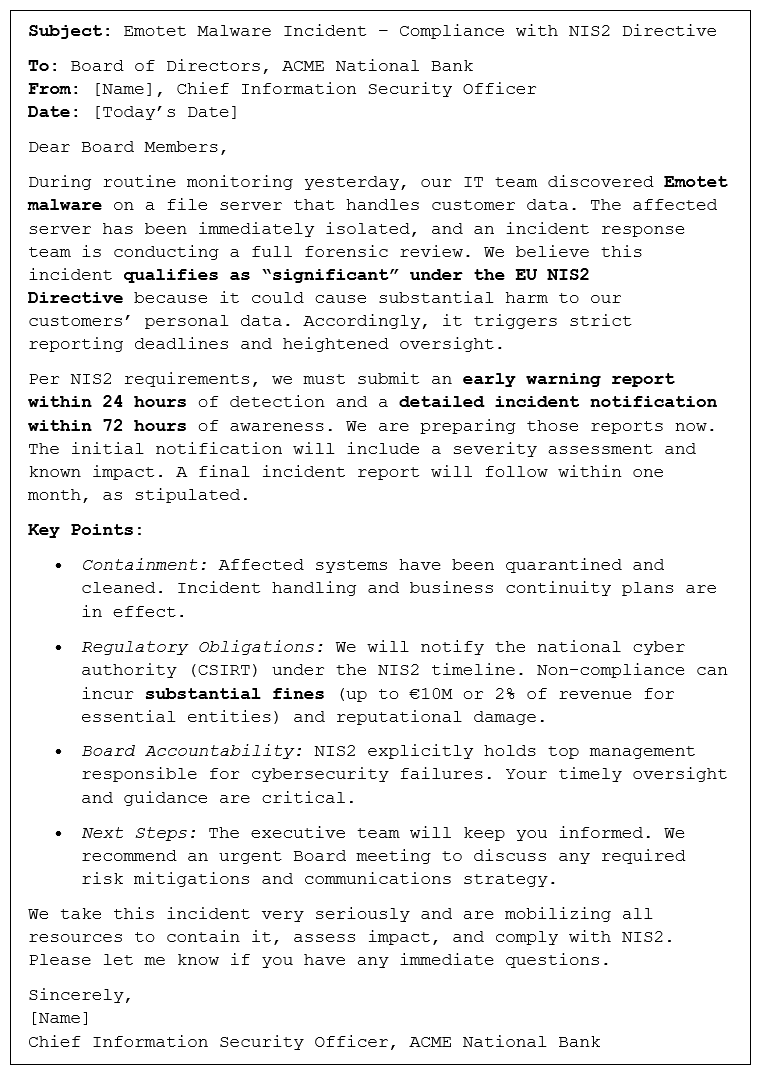
This log of actions aligns with NIS2’s incident handling requirements. For example, industry guidance emphasizes isolating affected systems and preserving evidence while keeping stakeholders informed. ACME’s response adhered to these practices and prepared all communications mandated by Article 23.
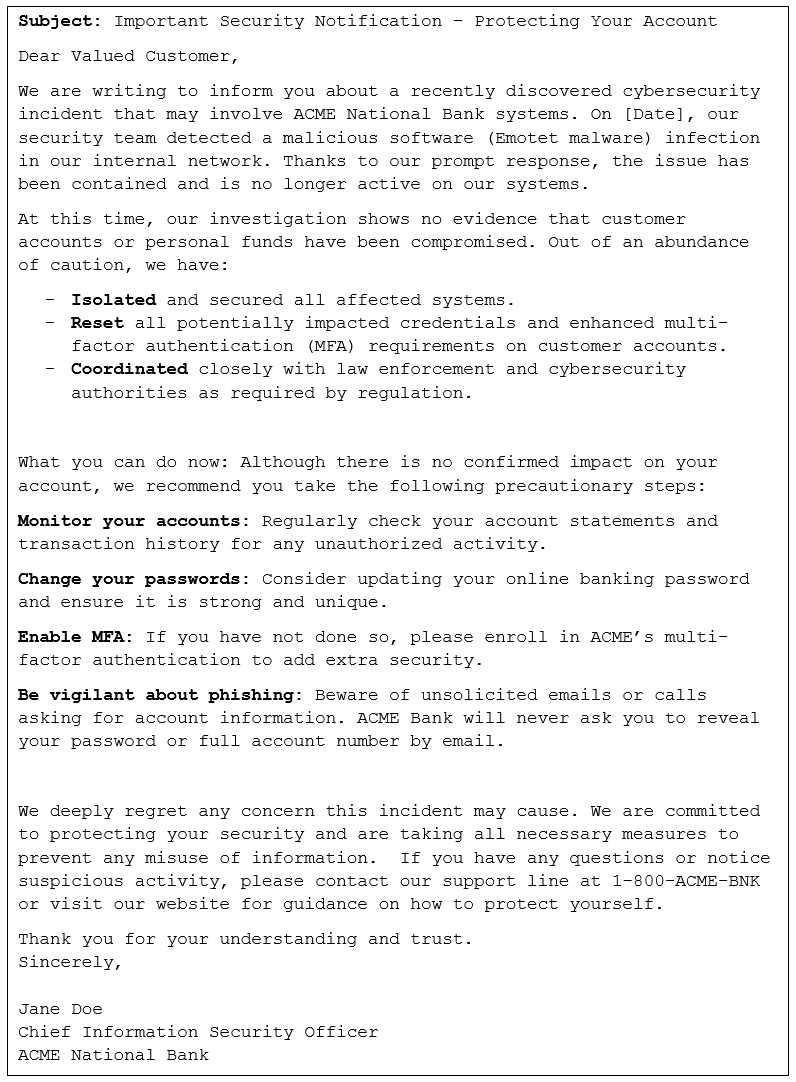
Draft Customer Advisory Email
In compliance with NIS2 Article 23, ACME Bank is obligated to notify customers of significant incidents that may affect their services. The following is a draft email from ACME Bank to its customers.
This advisory succinctly explains the situation and gives clear protective measures. It reflects NIS2’s requirement to communicate threats and remedies to affected service recipients. By notifying customers promptly and advising them to enable MFA and monitor accounts, ACME fulfills its obligation to keep users informed.
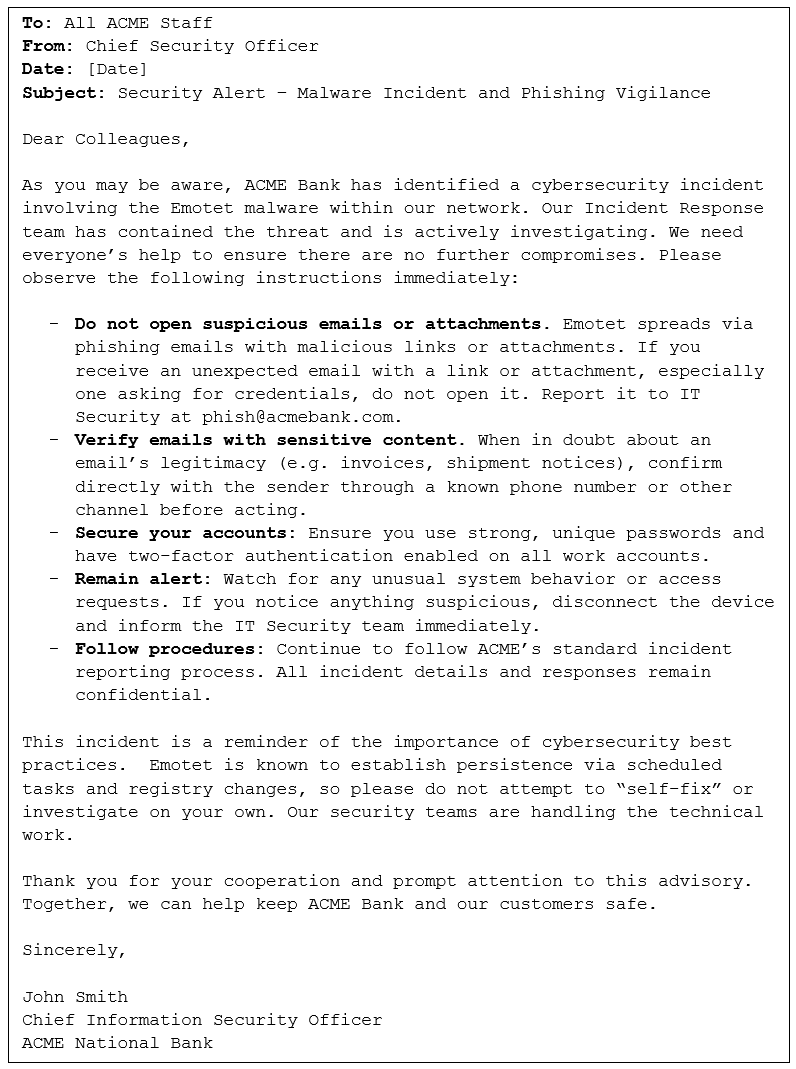
Draft Internal Staff Advisory
ACME Bank also issues an internal advisory to all employees to raise awareness and ensure vigilance.
This staff advisory alerts employees to the threat and instructs them on vigilance. It incorporates lessons from Emotet’s known behavior (spread by email and persistence mechanisms) and reinforces protective actions. By communicating clearly with staff, ACME supports its internal incident handling (Article 21) and ensures everyone understands their role in the response.
72-Hour Incident Notification Report (National CSIRT)
Incident Summary: On [Date 1], ACME Bank detected a significant malware intrusion (Emotet trojan) affecting our internal network. The trojan was introduced via a phishing email and had the potential to disrupt banking services. The incident is considered significant under NIS2 because it poses risk of severe operational disruption and potential financial harm. The bank’s cybersecurity team immediately isolated infected systems and began remediation.
Timeline: The incident was discovered at 09:00 on [Date 1]. An early warning was submitted to our national CSIRT within 24 hours, reporting that the incident was caused by malicious software and had no known cross-border impact. Key actions in the first 72 hours are summarized in the Containment Actions Log (above). By [Date 3, 09:00], all known malicious activity was contained.
Initial Impact Assessment (Severity & Scope): Emotet’s presence prompted a precautionary shutdown of several internal services. At peak, approximately 15 workstations and servers showed indicators of compromise (emails forwarded, processes running). No core banking systems were taken offline. There is currently no confirmed unauthorized access to customer accounts or evidence of customer data exfiltration; however, potential exposure of employee credentials and internal documentation remains under investigation. We estimate the incident’s impact as moderate: it has not halted critical services, but required urgent action and carries reputational risk. This preliminary assessment of severity and impact is provided in compliance with NIS2 Article 23.
Root Cause: The breach was caused by an Emotet banking Trojan delivered via a spear-phishing email. Emotet is a polymorphic downloader that spreads rapidly through networks. Our analysis indicates an employee opened a malicious attachment, allowing Emotet to install and begin propagating using collected credentials. Emotet’s dropper modules were able to harvest passwords and attempt lateral movement. All signatures of Emotet infection (scheduled tasks, registry entries, running services) were identified and removed.
Mitigation Measures Taken: We have executed comprehensive containment steps:
-
Isolation: Disconnected all infected endpoints and blocked malicious C2 domains.
-
Eradication: Removed Emotet processes, scheduled tasks, and registry entries on compromised machines.
-
Recovery: Systems were reimaged or rebuilt from clean backups. Patches were applied for all critical vulnerabilities.
-
Credential Changes: All potentially affected user and admin passwords have been reset, and network-wide MFA has been enforced.
-
Monitoring: Enhanced logging and network monitoring remain in place. We are reviewing historical logs for any lateral movement or data access.
-
Communications: Customers, regulators, and staff have been informed as per our incident response plan.
Remaining Actions and Outlook: The incident is currently contained. IR teams continue analysis to confirm no data was exfiltrated. We will cooperate with law enforcement on any criminal investigation. A final incident report, including detailed post-incident analysis and lessons learned, will be submitted within one month as required.
Cross-Border Impact: At present, we have no indication that the incident affected systems or customers outside our country.
Please contact ACME Bank’s CSIRT liaison ([email protected]) for further information or interim updates.
Sincerely,
Emily Johnson
Director of Cybersecurity Operations
ACME National Bank